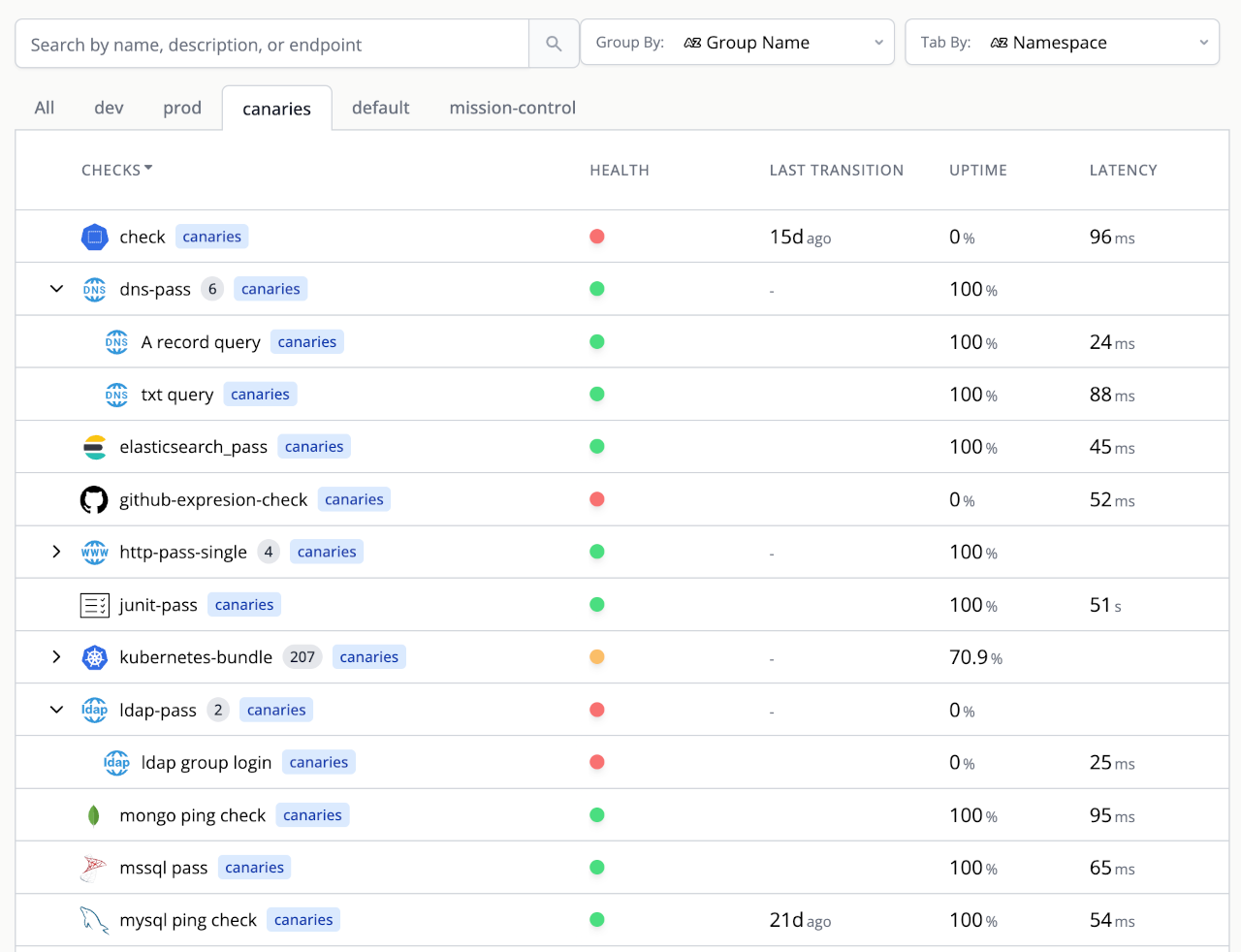
A single pane of glass for health across your stack.
Aggregate alerts, run synthetic checks / tests against your services and infrastructure.
Synthetic (Active) Checks
Generate synthetic traffic, run queries against various datasources, or even run full integration test suites to verify the health of your services and infrastructure.
Passive Checks
Consolidate alerts across your monitoring stack and create alerts from non-traditional sources like SQL, NoSQL and CI/CD pipelines.
Infrastructure
Batteries including support for HTTP, DNS, ICMP, LDAP, Prometheus, SQL, Mongo, Redis, Github, Azure Devops, JMeter, K6, Playwright, Newman/Postman, SMB, SFTP,
Integrations
Batteries included with 30+ check types
Canary checker is a single binary with most checks bundled and not requiring an external installation.
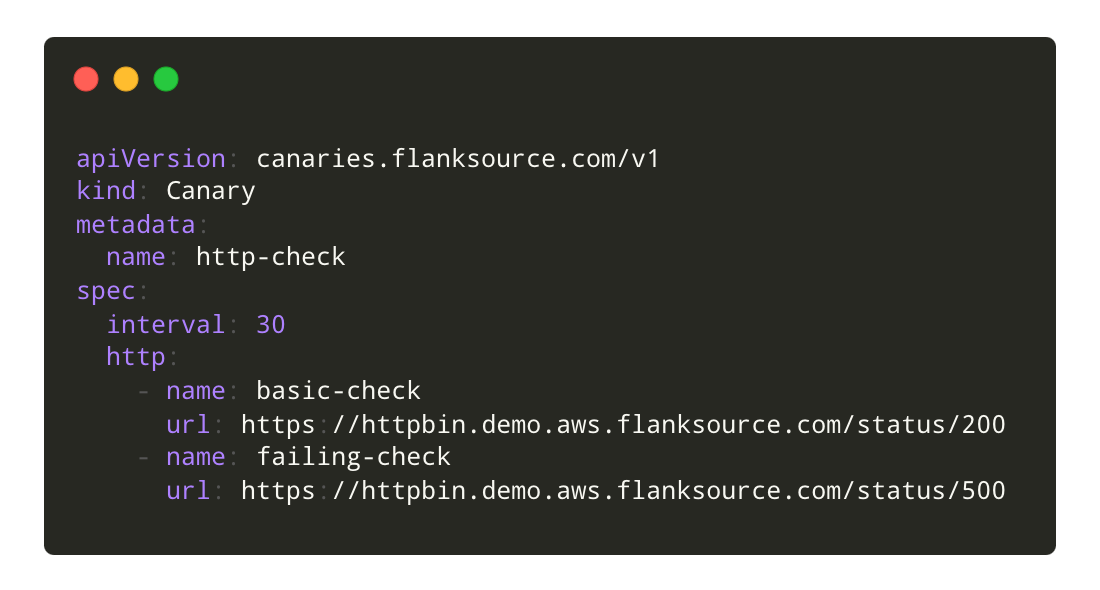
Kubernetes Native
Health Checks as Code
Canaries are regular Kubernetes Custom Resource Definitions with conformant status conditions, making it suitable to use as Flux, ArgoCD or Helm health check.
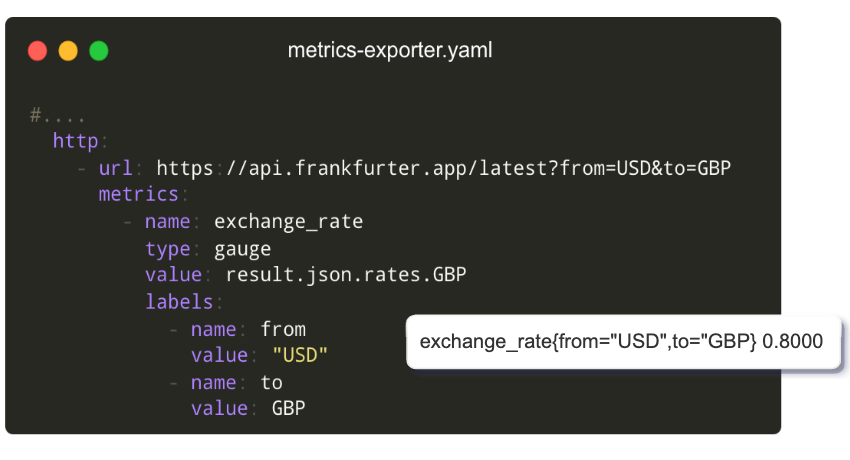
Prometheus
Metrics Exporter
Export custom metrics from any check, replacing the need for multiple separate metric exporters.
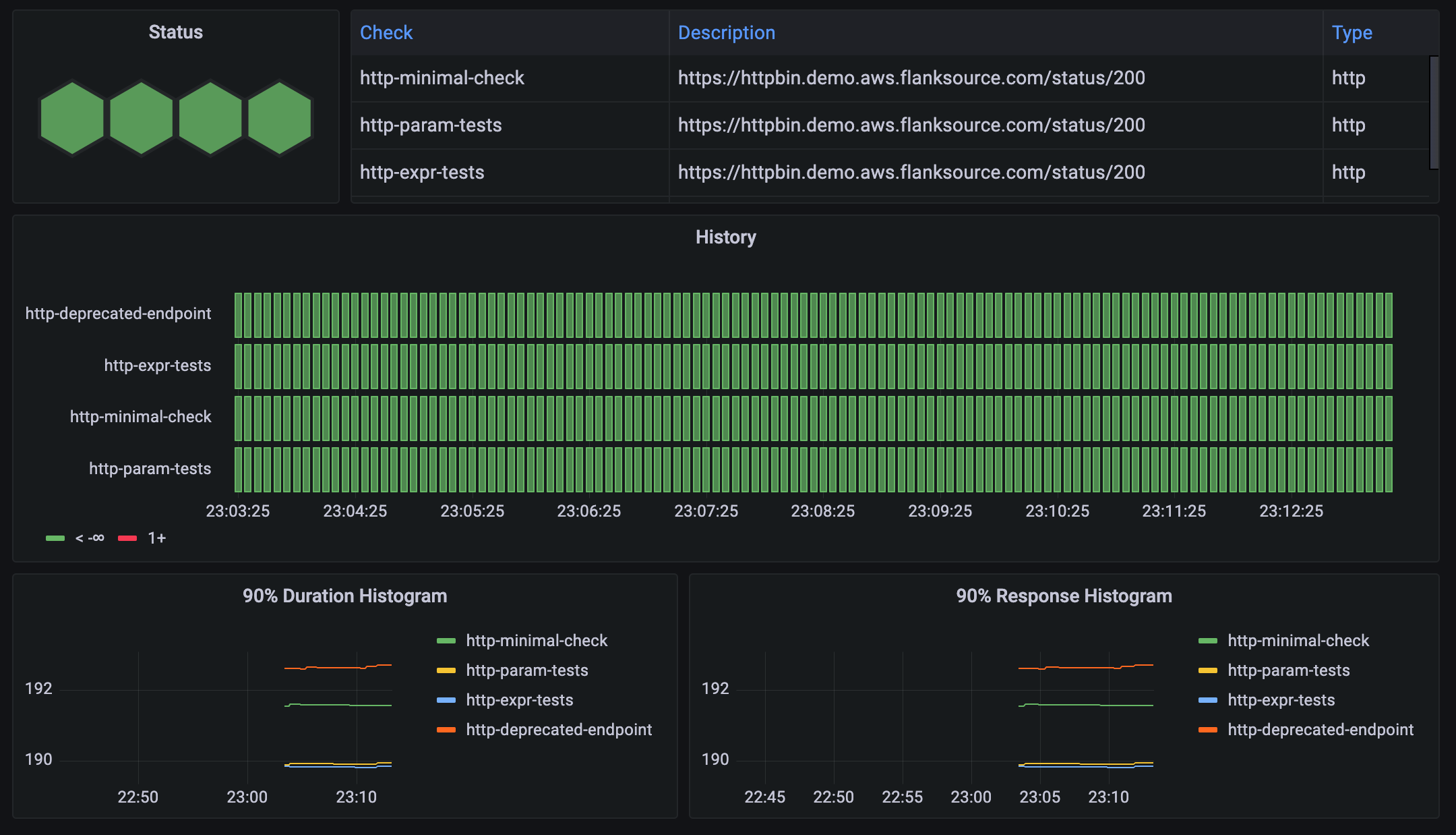
Dashboards
Grafana
Chose from a standard Grafana dashboard or create your own using the prometheus metrics exposed by Canary Checker.
Context
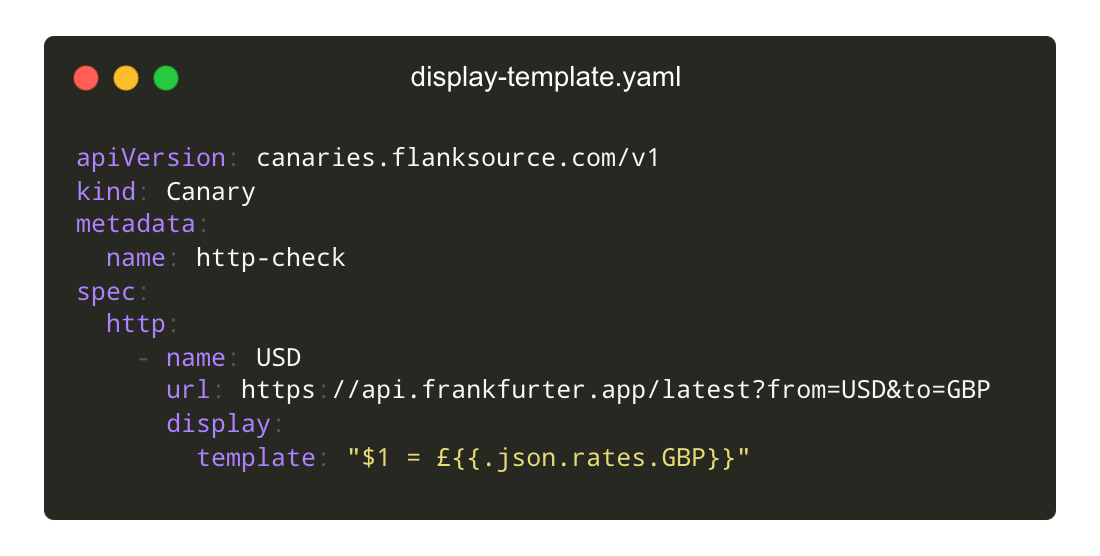
Display Formatted Output
Evaluate the health of checks using scripts in CEL, Javascript or Go Templating. Templates can also be used to format the output of checks.
Escape Hatch
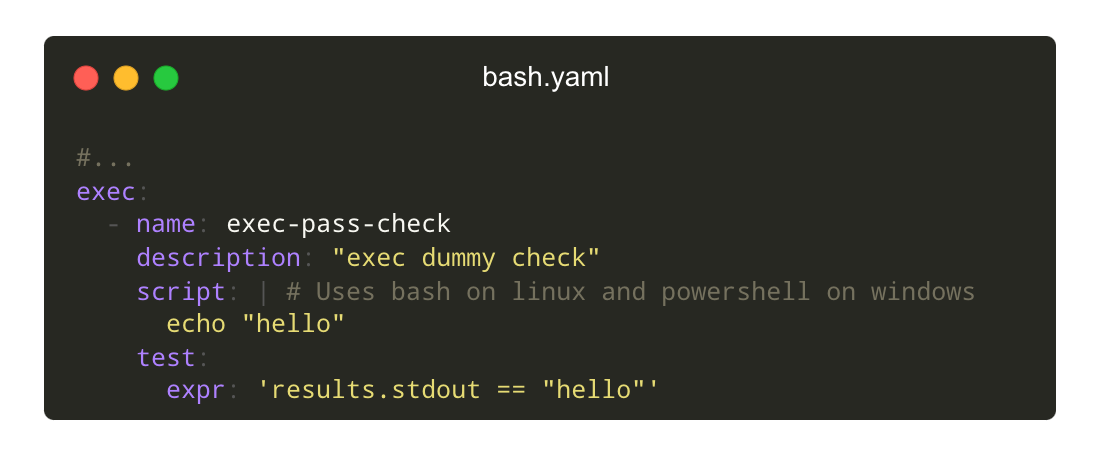
Fallback to shell scripts
When the builtin integrations are not enough, run scripts using bash or powershell.
Control Plane Monitoring
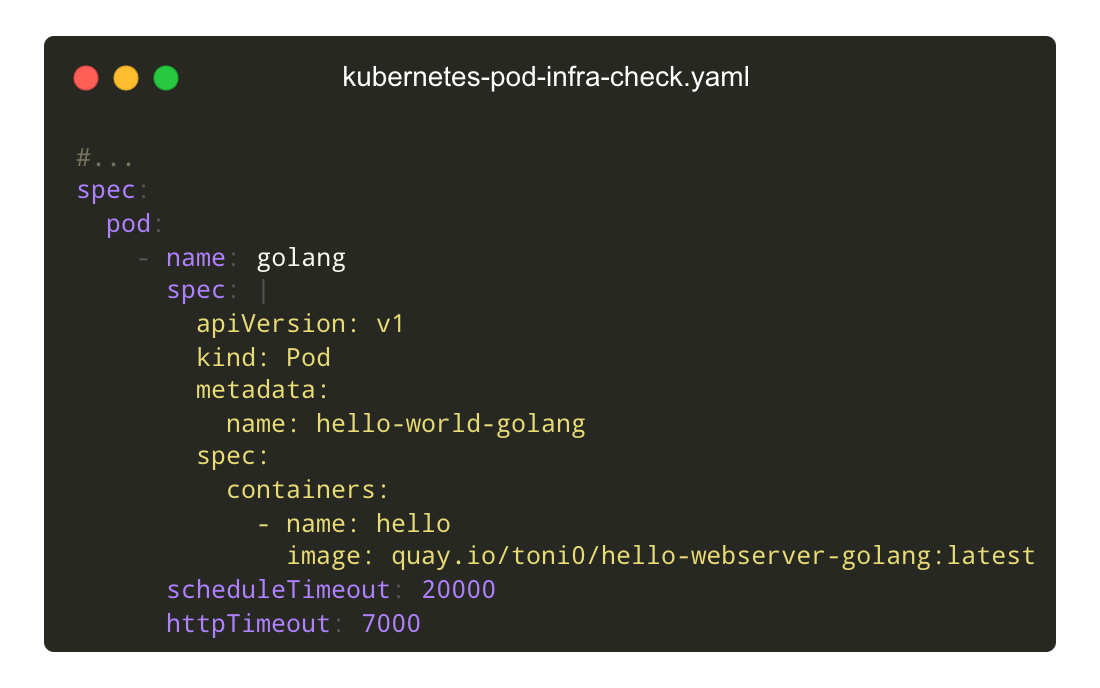
Active Infrastructure Checks
Proactive infrastructure checks ensure your control plane has ample buffer/ or capacity. These checks validate the ability to schedule new pods, launch EC2 instances, and push/pull to docker and helm repositories.

Escape Hatch
Scripting
Evaluate the health of checks using scripts in CEL, Javascript or Go Templating. Templates can also be used to format the output of checks.
Secret Management
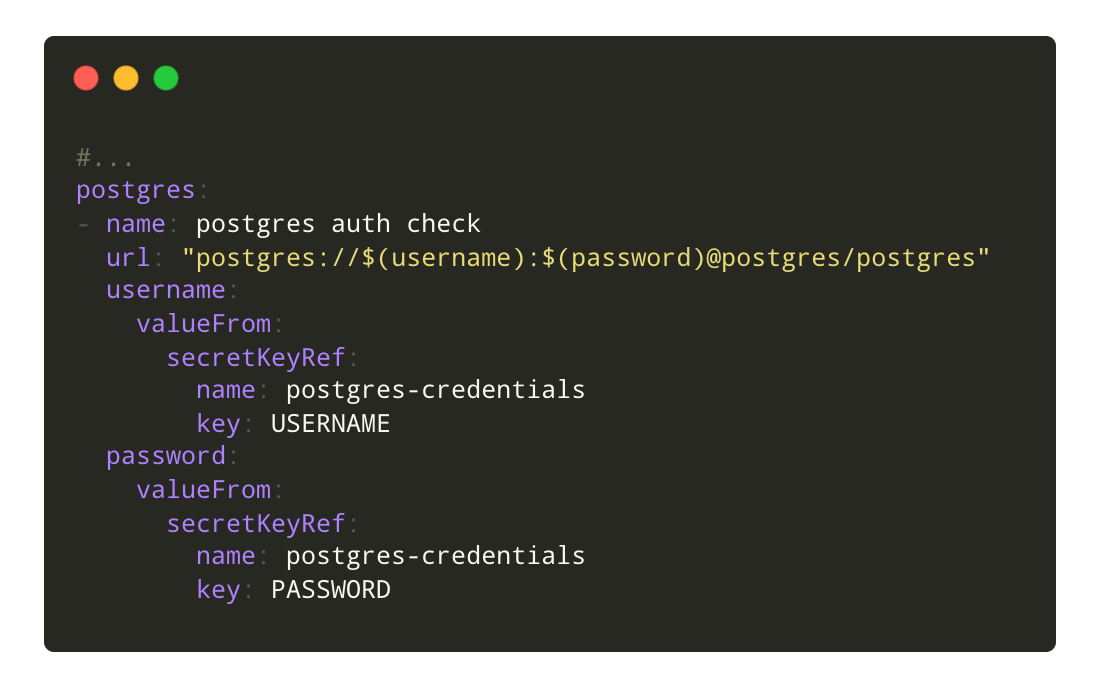
Leverage Kubernetes Secrets
Canaries are namespace aware and can be configured to use kubernetes secrets and configmaps for authentication details, negating the need to store secrets in the configuration.
Support
Support for Canary Checker is available as part of the Flanksource Mission Control Internal Developer Platform
- SaaS Hosted Platform on either AWS or Azure
- On Premise Run inside your own data center or Bring Your Own Cloud
- Resource Catalog & Change Tracking Track both application and infrastructure resources across multiple clouds.
- Playbooks Run automated playbooks based on canary checker health changes
- Notifications Send notifications to 10+ different targets when canaries fail
- Topology Map your complex system in multiple dimensions






